这篇文章记录一下Remnawave节点的安装与配置。
先简单介绍一下Remnawave节点的工作方式,Remnawave节点是通过面板下发配置来运行的,也就是我们在面板内手搓Xray-core的配置文件(或者使用官方的配置模板),然后节点会获取到面板的Xray-core配置文件,之后节点根据Xray-core配置文件内的设置来运行。
Xray-core本身是支持非常多的协议与传输方式的,这些协议与传输方式大多数Remnawave都是支持的,但是有一些例外,比如ss现在还不支持2022。在这种情况下,这篇文章我只列出几个具有典型参考价值的配置示例:
Shadowsocks(配置起来最简单)
VLESS-TCP-REALITY(不需要SSL证书)
VLESS-XHTTP-REALITY(不需要SSL证书)
VLESS-XHTTP-TLS(可过CDN,需要SSL证书)
Trojan-Websocket-TLS (可过CDN,需要SSL证书,但是已经被Xray-core弃用,建议用XHTTP)
首先登录Remnawave面板,找到配置文件:
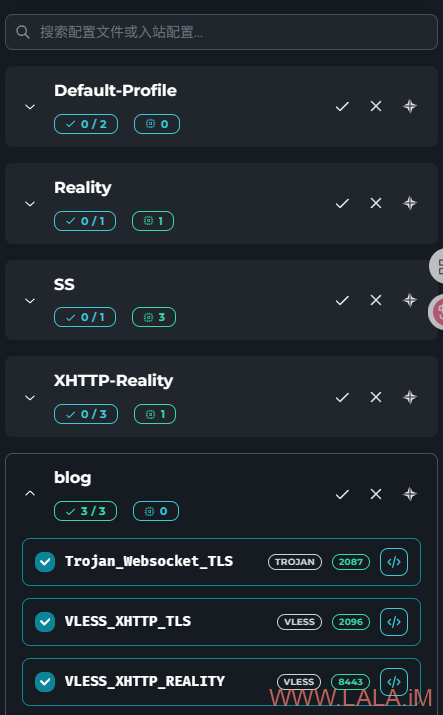
创建新的配置文件:
Shadowsocks示例配置:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "Shadowsocks_97591",
"port": 51888,
"protocol": "shadowsocks",
"settings": {
"clients": [],
"network": "tcp,udp"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
VLESS-TCP-REALITY示例配置:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "VLESS_TCP_REALITY",
"port": 443,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "raw",
"security": "reality",
"realitySettings": {
"show": false,
"xver": 0,
"target": "www.cloudflare.com:443",
"shortIds": [
""
],
"privateKey": "填写面板生成的私钥",
"serverNames": [
"www.cloudflare.com"
]
}
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
VLESS-XHTTP-REALITY示例配置:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "VLESS_XHTTP_REALITY",
"port": 8443,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "xhttp",
"security": "reality",
"xhttpSettings": {
"host": "",
"mode": "auto",
"path": "/fuckgfw_0x000008964"
},
"realitySettings": {
"target": "www.cloudflare.com:443",
"shortIds": [
""
],
"privateKey": "填写面板生成的私钥",
"serverNames": [
"www.cloudflare.com"
]
}
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
VLESS-XHTTP-TLS示例配置:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "VLESS_XHTTP_TLS",
"port": 2096,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "xhttp",
"security": "tls",
"tlsSettings": {
"alpn": [
"h3",
"h2",
"http/1.1"
],
"minVersion": "1.2",
"serverName": "xhttp.example.com",
"certificates": [
{
"keyFile": "/var/lib/remnawave/configs/xray/ssl/xhttp.example.com.key",
"certificateFile": "/var/lib/remnawave/configs/xray/ssl/xhttp.example.com.pem"
}
]
},
"xhttpSettings": {
"host": "xhttp.example.com",
"mode": "auto",
"path": "/fuckgfw_0x000008964"
}
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
Trojan-Websocket-TLS示例配置:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "Trojan_Websocket_TLS",
"port": 2087,
"protocol": "trojan",
"settings": {
"clients": []
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "ws",
"security": "tls",
"wsSettings": {
"host": "trojan.example.com",
"path": "/ws",
"headers": {}
},
"tlsSettings": {
"minVersion": "1.2",
"certificates": [
{
"keyFile": "/var/lib/remnawave/configs/xray/ssl/trojan.example.com.key",
"certificateFile": "/var/lib/remnawave/configs/xray/ssl/trojan.example.com.pem"
}
],
"cipherSuites": "TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"rejectUnknownSni": true
}
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
一个配置文件可以有多个入站,也就是说你可以把刚才的这些示例配置整合在一个配置文件内,这样一个节点就可以同时选择多个入站,让一个节点同时支持多种协议、传输方式。
例如我可以将上面的VLESS-XHTTP-REALITY、VLESS-XHTTP-TLS、Trojan-Websocket-TLS都配置在一个配置文件内:
{
"log": {
"loglevel": "info"
},
"inbounds": [
{
"tag": "Trojan_Websocket_TLS",
"port": 2087,
"protocol": "trojan",
"settings": {
"clients": []
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "ws",
"security": "tls",
"wsSettings": {
"host": "trojan.example.com",
"path": "/ws",
"headers": {}
},
"tlsSettings": {
"minVersion": "1.2",
"certificates": [
{
"keyFile": "/var/lib/remnawave/configs/xray/ssl/trojan.example.com.key",
"certificateFile": "/var/lib/remnawave/configs/xray/ssl/trojan.example.com.pem"
}
],
"cipherSuites": "TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"rejectUnknownSni": true
}
}
},
{
"tag": "VLESS_XHTTP_TLS",
"port": 2096,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "xhttp",
"security": "tls",
"tlsSettings": {
"alpn": [
"h3",
"h2",
"http/1.1"
],
"minVersion": "1.2",
"serverName": "xhttp.example.com",
"certificates": [
{
"keyFile": "/var/lib/remnawave/configs/xray/ssl/xhttp.example.com.key",
"certificateFile": "/var/lib/remnawave/configs/xray/ssl/xhttp.example.com.pem"
}
]
},
"xhttpSettings": {
"host": "xhttp.example.com",
"mode": "auto",
"path": "/fuckgfw_0x000008964"
}
}
},
{
"tag": "VLESS_XHTTP_REALITY",
"port": 8443,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
]
},
"streamSettings": {
"network": "xhttp",
"security": "reality",
"xhttpSettings": {
"host": "",
"mode": "auto",
"path": "/fuckgfw_0x000008964"
},
"realitySettings": {
"target": "www.cloudflare.com:443",
"shortIds": [
""
],
"privateKey": "填写面板生成的私钥",
"serverNames": [
"www.cloudflare.com"
]
}
}
}
],
"outbounds": [
{
"tag": "DIRECT",
"protocol": "freedom"
},
{
"tag": "BLOCK",
"protocol": "blackhole"
}
],
"routing": {
"rules": []
}
}
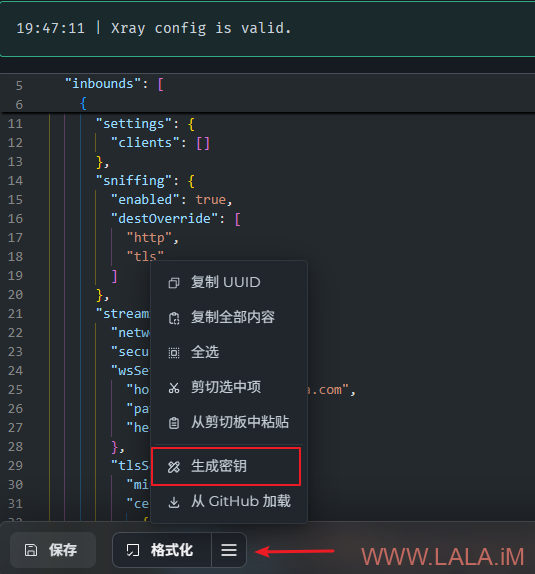
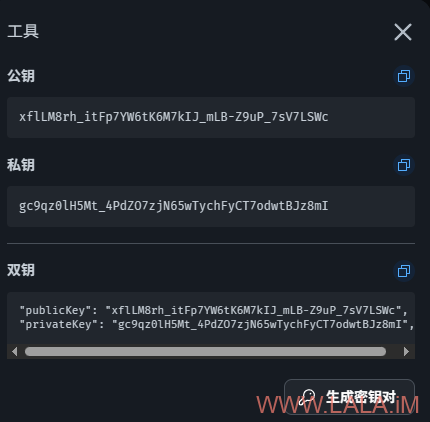
其中使用REALITY的配置需要生成密钥对,可以通过面板的“生成密钥”功能生成:
在面板的配置文件中只需要把生成的私钥填写上去,公钥面板会通过订阅自动配置给客户端不需要管:
对于需要使用SSL证书的节点,需要在Remnawave面板的后端服务内添加一个bind mount,将SSL证书挂载到容器内。Remnawave面板会将节点需要用到的SSL证书发送给相应节点。
在Remnawave面板项目目录内新建一个ssl目录用于存放SSL证书:
cd /opt/remnawave mkdir ssl
然后编辑compose文件:
nano docker-compose.yml
添加bind mount,示例配置:
...
remnawave:
image: remnawave/backend:latest
container_name: 'remnawave'
hostname: remnawave
restart: always
ports:
- '127.0.0.1:3000:3000'
env_file:
- .env
networks:
- remnawave-network
volumes:
- ./ssl:/var/lib/remnawave/configs/xray/ssl
healthcheck:
test: ['CMD-SHELL', 'curl -f http://localhost:${METRICS_PORT:-3001}/health']
interval: 30s
timeout: 5s
retries: 3
start_period: 30s
depends_on:
remnawave-db:
condition: service_healthy
remnawave-redis:
condition: service_healthy
...
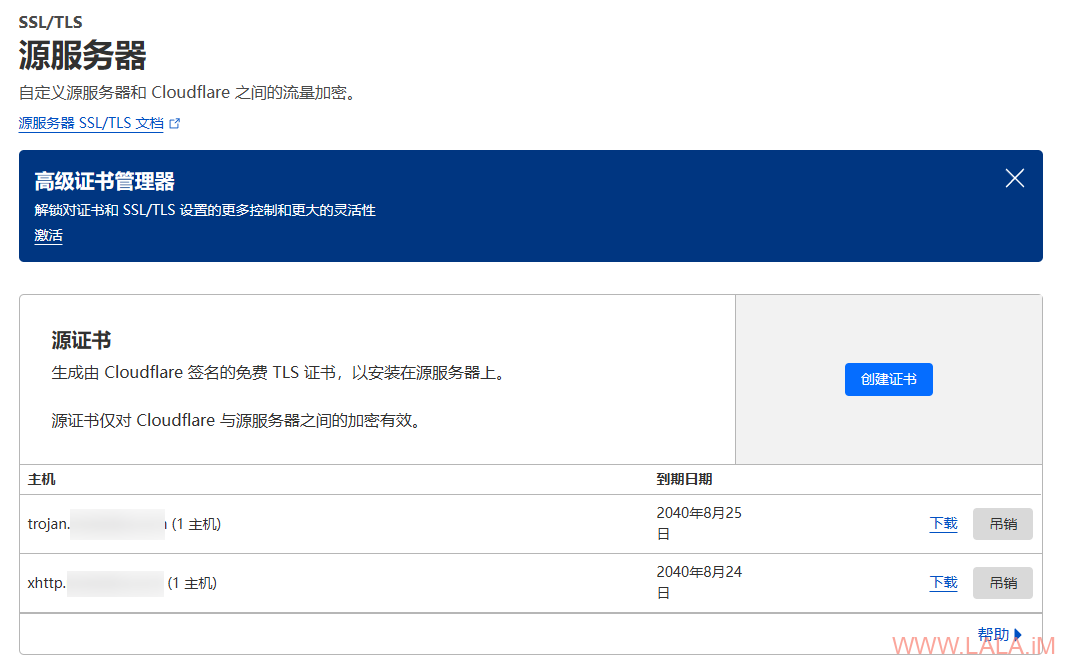
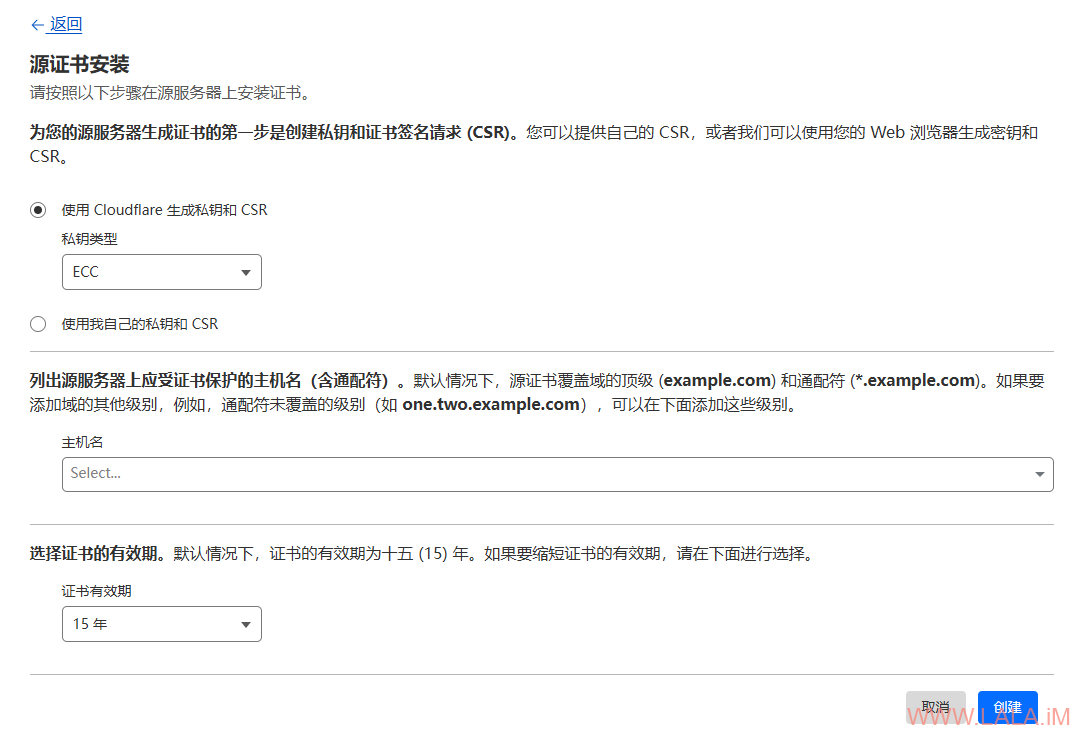
这些可以过CDN的配置(VLESS-XHTTP-TLS、Trojan-Websocket-TLS)我个人建议直接使用CloudFlare的源证书,一次申请可以用15年,后续几乎不用维护:
将申请好的证书和私钥分别保存到ssl目录下,例如:xhttp.example.com.key、xhttp.example.com.pem。文件名务必与之前在配置文件内的保持一致。
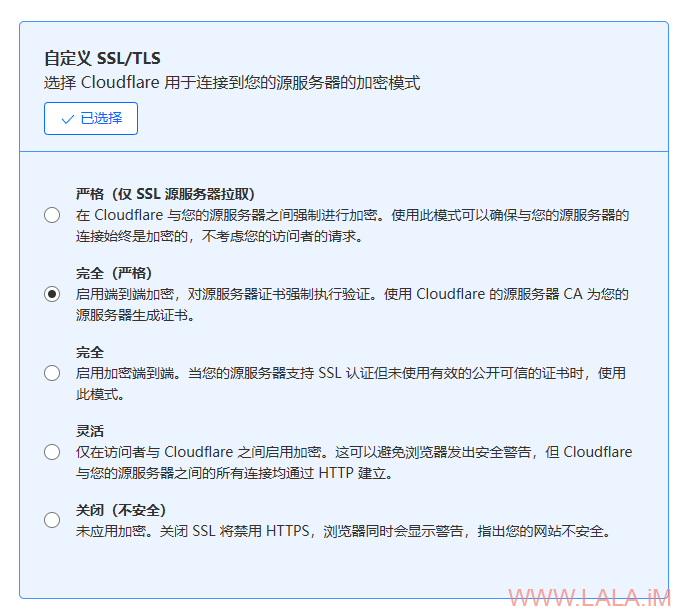
同时务必在CloudFlare内将SSL/TLS模式选择为完全(严格):
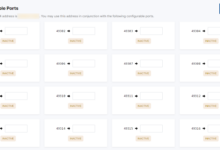
另外请注意CloudFlare回源有端口限制,HTTPS仅支持以下端口:
443
2053
2083
2087
2096
8443
配置好证书后重启面板:
docker compose down docker compose up -d
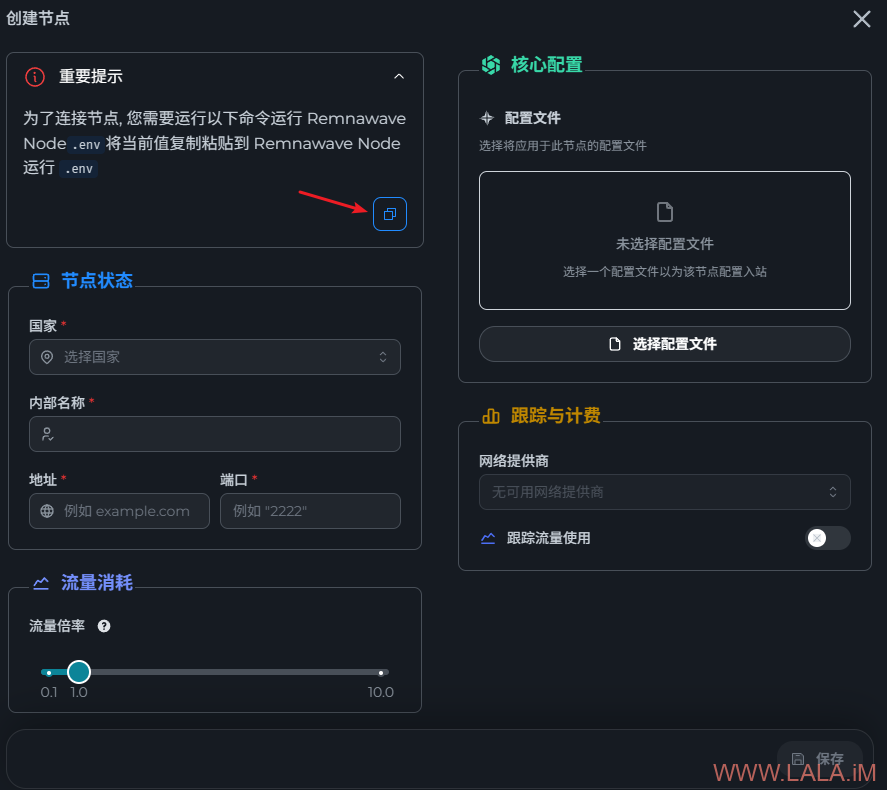
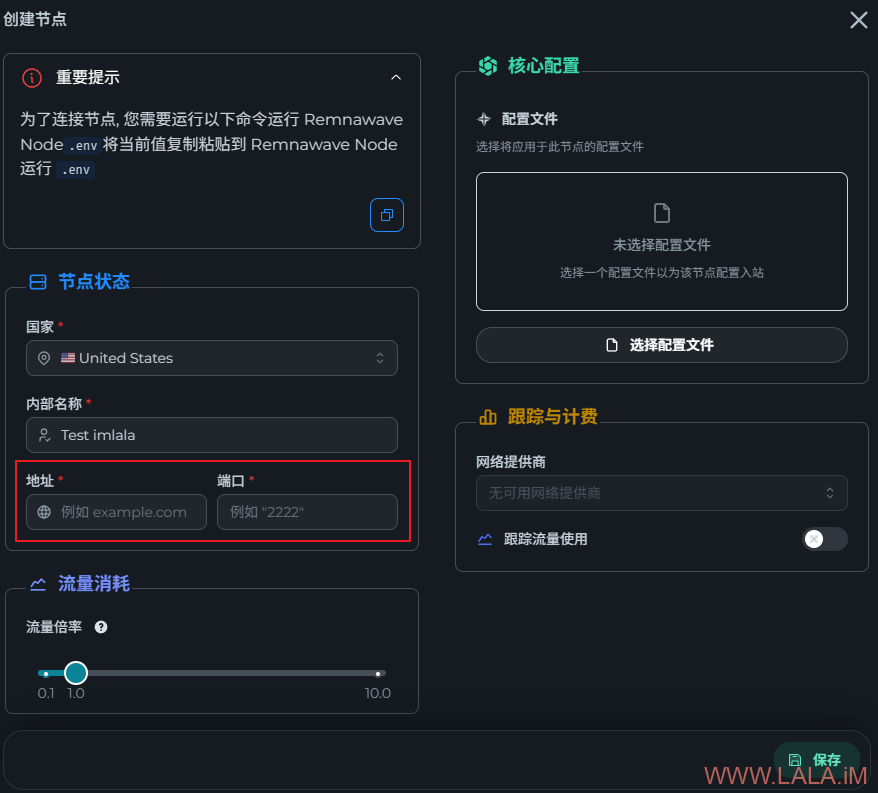
回到面板内,找到节点–>管理,现在尝试创建一个节点,点击如图所示按钮将复制下来的内容保存好待会需要用到:
现在来安装节点,首先在节点服务器上也需要安装Docker:
apt -y update apt -y install curl curl -fsSL https://get.docker.com -o get-docker.sh sh get-docker.sh
创建目录:
mkdir /opt/remnanode && cd /opt/remnanode
创建.env文件:
nano .env
写入如下配置,其中SSL_CERT=后面的内容是之前你在面板上复制的,粘贴到这里即可:
APP_PORT=22222 SSL_CERT=CERT_FROM_MAIN_PANEL
创建compose文件:
nano docker-compose.yml
写入如下配置:
services:
remnanode:
container_name: remnanode
hostname: remnanode
image: remnawave/node:latest
restart: always
network_mode: host
env_file:
- .env
启动节点服务:
docker compose up -d
回到面板内,填写节点服务器的IP地址与端口,端口是之前在.env配置文件内设置的22222端口:
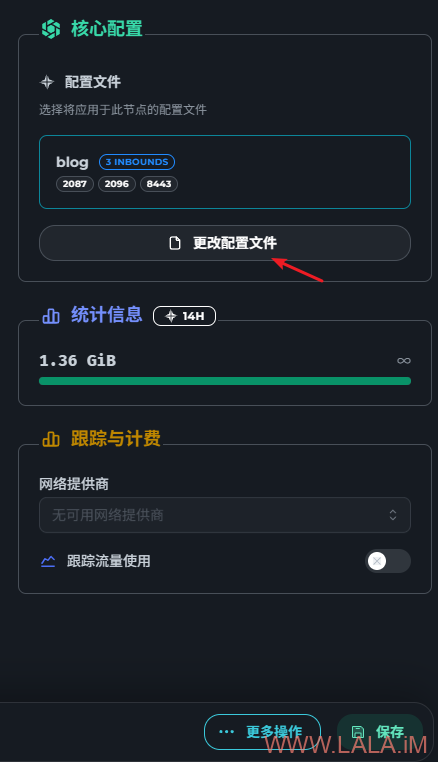
点击更改配置文件,选择之前创建的配置,可以选择一个配置文件内的单个或多个入站(如果有的话)但不能同时选择多个配置文件:
这里我为了演示就把之前的三个入站都勾选上:
等待片刻,如果一切正常,面板上面应显示节点是在线状态:
如果节点连接不上,除了网络问题外,一般是Xray-core配置有误,可以通过下面的命令来检查remnanode容器的日志:
docker compose logs -f
如果看到有类似这样的错误提示,则可以确定是Xray-core配置有误:
XML-RPC fault: SPAWN_ERROR: xray
然后使用下面的命令来查看Xray-core的日志,根据Xray-core的日志信息来解决相应的问题:
docker exec -it remnanode tail -n +1 -f /var/log/supervisor/xray.out.log
这篇文章就先写到这里,下篇文章介绍Remnawave订阅相关的内容。
 荒岛
荒岛



LALA你好,想問一下,在VLESS-XHTTP-REALITY設置中,為何我加上了shortID(比如”ai”,”0123456789abcdef”,等等),連接時就會顯示ssl error;shortID留空時就沒有問題?
另外,根據官方example,建議在server setting的routing採用“禁回國流量的路由規則”
順便問一下,LALA自己平時一般主要用那種協議配置組合?
ssl error我也不知道,我没有加这个id,因为文档上写的可以留空。协议的话怎么说呢,看需求和场景吧。机器线路差就用hy2,ip被墙了就用能过cdn的,打游戏我用ss,线路好的机器我用anytls或者reality,其实我用的最多的就是ss,然后xhttp我只是折腾尝尝鲜,还没有正式使用。
短id那块,是不是你配置有问题,用这个命令生成看看?openssl rand -hex 8
wow, openssl rand -hex 8可以了⋯⋯原來不是所有的【00…0】到【FF…F】都可以的,我原本就隨便寫了幾個2/4/8/16位的16進制數字⋯⋯謝謝LALA!
2025/09/15 18:29:14.998492 [Info] transport/internet/splithttp: failed to validate host, request:154.83.91.114:2096, config:xhttp.safetun.bar
我已经把SSL 添加了目录了 为什么会这样呢
你给的信息太少了,看不出来哪里的问题。只能给点提示你:ssl是配置在面板端不是节点端。注意证书和key的格式,最好用pem。再就是先裸连测试不要直接一上来就套cdn。。
官方的ssl配置文档,你可以看下:https://remna.st/docs/install/remnawave-node#xray-ssl-cert-for-node
你好,我想请教一下,这个为什么添加不了ipv6鸡,他无法连接到面板鸡的xray配置
学习了,感谢博主。